
Passkeys & Building User Trust
When was the last time you checked your password security?
In a world where digital threats loom large, securing data and identities has never been more critical. This presentation dives into the current landscape of passkey adoption, shedding light on how we can prioritize user trust and understanding to empower users in securing their digital identity through passkeys.
Role
UX/UI Designer
UX Researcher
Time
10-12 Weeks
Responsibility
UX research, UX/UI design, UX strategy
Phase
.png)
Background
In January 2024, Forbes reported a massive breach involving major companies, exposing 12 terabytes of sensitive information, including passwords. Astra's findings indicate that in 2021, nearly 83% of companies reported experiencing phishing attacks, and shockingly, 22% of all breaches resulted from phishing scams. Also, according to CBS News, United Healthcare also faced a significant data breach in February 2024 due to a credential stuffing attack.
The frequencies of these breaches are alarming and underscore a critical need for enhanced security measures in the digital realm. This is where passkeys come in -
groundbreaking authentication technology designed to offer a more secure alternative to traditional authentication methods.
How passkeys work
Passkeys use unique biometric data, such as fingerprints or facial recognition.
Once you create passkeys, two keys will be generated: A “public” and a “private” key. The private key with your biometrics stays on your device, and the public key with cryptographic keys stays on the website or app. You need both keys need to pair to authenticate.

Possession based
+
Knowledge-based
Possession based
+
Inherence-based
Knowledge-based – something you know = passwords
Possession-based – something you have = code sent to your phone, device
Inherence-based – something you are = biometric

Device unlocks via biometric (face ID or fingerprint)
Completes a handshake that represents the private key
This handshake is then matched to the public key.
According to Daniel from Corbado.com, there
are three common factors of authentication: knowledge-based, possession-based, and inherence-based.
Passkeys incorporate possession-based factors like your device and inherence-based factors like your biometrics, a more powerful authentication combination.
Discovery
Literature review
The literature review revealed that there has been a slow adaptation of passkeys due to three key factors:
Familiarity and Perceived adequacy

-
Necessity is a top obstacle for passkey adoption.
-
Traditional methods like 2FA are seen as sufficient by users.
-
Companies are also facing challenges in deployability and financial considerations
User trust and self-efficacy in
biometric systems

-
Challenges hindering the implementation of biometrics
-
Concerns about privacy
-
Ease and perceived security of biometrics
-
Self-efficacy to interact with biometrics efficiently
-
Readability and transparency

-
Declined readability post-GDPR
-
Standardization of language = may impede user comprehension
-
Large quantity of new information
Discovery
User survey
After the literature review, I formed a hypothesis that if users are educated about the higher security level of passkeys over traditional methods and assured that biometrics stays locally on their device, they will be more willing to adopt passkeys.
To support this hypothesis, I launched a user survey that began with an educational segment that highlighted the security advantages of passkeys and emphasized that biometrics stay on users' devices.
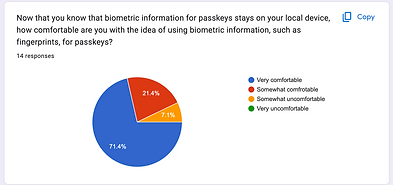
Enhanced user confidence through education
71.4% of respondents expressed an increased sense of security and willingness to move forward with passkeys.
Transparency and user control provide confidence in biometrics
Users want transparent assurance that biometrics stays on the local device and is not shared with anyone.

Defining the problem statement
Traditional authentication methods are highly vulnerable to phishing and other cybercrime. There is a need to create efficient passkey education streams to educate users on the advantages of passkey over traditional methods and foster increased understanding and trust to enhance their digital security.
Ideating Design Solutions
Help page
-
Empower users and instill confidence through a more personalized, interactive education experience
-
Ensure transparency about how biometric data is used
-
Anchor menus and search bars to ease navigation through the large amount of content
-
Information on opt-in and opt-out options

Marketing campaign
-
Provide current security level assessment and encourage users to take security measures with passkeys
-
Compatibility quiz / gamify educational content
-
Raise awareness about the benefits and security of passkeys

Enhancing user experience
-
Integrating visuals to enhance understanding
-
Incorporate step-by-step instructions along with visuals as a guide
-
Place the benefits of biometric and data storage information at the forefront for visibility and transparency
-
Conversational language


